Having Trouble Uploading Photo to Twitter Using Tor Browser
Tor Browser
How can I verify Tor Browser's signature?
Digital signature is a process ensuring that a certain package was generated by its developers and has not been tampered with. Below we explain why it is of import and how to verify that the Tor Browser you download is the one nosotros accept created and has not been modified by some attacker.
Each file on our download page is accompanied past a file labelled "signature" with the same proper noun as the package and the extension ".asc". These .asc files are OpenPGP signatures. They permit y'all to verify the file you've downloaded is exactly the ane that we intended you to go. This will vary by web browser, but more often than not you tin download this file past right-clicking the "signature" link and selecting the "save file as" choice.
For example, torbrowser-install-win64-9.0_en-US.exe is accompanied by torbrowser-install-win64-9.0_en-US.exe.asc. These are example file names and will non exactly match the file names that you download.
We now show how you can verify the downloaded file's digital signature on different operating systems. Delight notice that a signature is dated the moment the package has been signed. Therefore every time a new file is uploaded a new signature is generated with a different appointment. As long as you accept verified the signature you lot should not worry that the reported date may vary.
Installing GnuPG
Get-go of all you demand to have GnuPG installed before you lot can verify signatures.
For Windows users:
If y'all run Windows, download Gpg4win and run its installer.
In guild to verify the signature you will need to type a few commands in windows control-line, cmd.exe.
For macOS users:
If you are using macOS, you tin can install GPGTools.
In order to verify the signature you lot will need to type a few commands in the Terminal (under "Applications").
For GNU/Linux users:
If y'all are using GNU/Linux, then yous probably already accept GnuPG in your system, equally well-nigh GNU/Linux distributions come with information technology preinstalled.
In club to verify the signature you will need to type a few commands in a final window. How to practice this will vary depending on your distribution.
Fetching the Tor Developers cardinal
The Tor Browser squad signs Tor Browser releases. Import the Tor Browser Developers signing fundamental (0xEF6E286DDA85EA2A4BA7DE684E2C6E8793298290):
gpg --auto-primal-locate nodefault,wkd --locate-keys torbrowser@torproject.org This should show you something like:
gpg: key 4E2C6E8793298290: public central "Tor Browser Developers (signing key) <torbrowser@torproject.org>" imported gpg: Full number processed: 1 gpg: imported: i pub rsa4096 2014-12-fifteen [C] [expires: 2025-07-21] EF6E286DDA85EA2A4BA7DE684E2C6E8793298290 uid [ unknown] Tor Browser Developers (signing primal) <torbrowser@torproject.org> sub rsa4096 2018-05-26 [S] [expires: 2020-12-19] If you become an mistake message, something has gone incorrect and you lot cannot continue until y'all've figured out why this didn't piece of work. You lot might be able to import the fundamental using the Workaround (using a public fundamental) section instead.
After importing the key, you can relieve it to a file (identifying it by its fingerprint here):
gpg --output ./tor.keyring --export 0xEF6E286DDA85EA2A4BA7DE684E2C6E8793298290 This command results in the key being saved to a file plant at the path ./tor.keyring, i.e. in the current directory. If ./tor.keyring doesn't exist afterwards running this command, something has gone wrong and you cannot continue until y'all've figured out why this didn't work.
Verifying the signature
To verify the signature of the package you downloaded, you will need to download the corresponding ".asc" signature file as well as the installer file itself, and verify it with a command that asks GnuPG to verify the file that you lot downloaded.
The examples below assume that yous downloaded these two files to your "Downloads" folder. Note that these commands utilize example file names and yours will exist different: you will have downloaded a unlike version than 9.0 and you may not have chosen the English (en-US) version.
For Windows users:
gpgv --keyring .\tor.keyring Downloads\torbrowser-install-win64-nine.0_en-The states.exe.asc Downloads\torbrowser-install-win64-nine.0_en-US.exe For macOS users:
gpgv --keyring ./tor.keyring ~/Downloads/TorBrowser-9.0-osx64_en-U.s..dmg.asc ~/Downloads/TorBrowser-nine.0-osx64_en-US.dmg For GNU/Linux users (change 64 to 32 if y'all have the 32-scrap parcel):
gpgv --keyring ./tor.keyring ~/Downloads/tor-browser-linux64-ix.0_en-US.tar.xz.asc ~/Downloads/tor-browser-linux64-9.0_en-United states of america.tar.xz The result of the control should produce something similar this:
gpgv: Signature made 07/08/19 04:03:49 Pacific Daylight Fourth dimension gpgv: using RSA key EB774491D9FF06E2 gpgv: Good signature from "Tor Browser Developers (signing key) <torbrowser@torproject.org>" If yous get error letters containing 'No such file or directory', either something went incorrect with one of the previous steps, or you forgot that these commands use example file names and yours will be a piddling different.
Workaround (using a public key)
If you lot see errors yous cannot fix, feel free to download and apply this public fundamental instead. Alternatively, you may apply the following command:
curl -s https://openpgpkey.torproject.org/.well-known/openpgpkey/torproject.org/hu/kounek7zrdx745qydx6p59t9mqjpuhdf |gpg --import - Tor Browser Developers cardinal is too bachelor on keys.openpgp.org and tin be downloaded from https://keys.openpgp.org/vks/v1/by-fingerprint/EF6E286DDA85EA2A4BA7DE684E2C6E8793298290. If y'all're using MacOS or GNU/Linux, the key can as well exist fetched past running the following control:
$ gpg --keyserver keys.openpgp.org --search-keys torbrowser@torproject.org
You lot may likewise want to learn more about GnuPG.
- Edit this page - Suggest Feedback - Permalink
How do I install Tor Browser?
How do I uninstall Tor Browser?
How do I update Tor Browser?
I downloaded and installed Tor Browser for Windows, only now I tin't detect it.
The file you download and run prompts you lot for a destination. If you lot don't remember what this destination was, it's most likely your Downloads or Desktop binder.
The default setting in the Windows installer besides creates a shortcut for y'all on your Desktop, though be aware that you may have accidentally deselected the choice to create a shortcut.
If you can't detect it in either of those folders, download it again and expect for the prompt that asks y'all to cull a directory to download it in. Choose a directory location that you'll call up easily, and once the download finishes you should see a Tor Browser folder at that place.
- Edit this page - Suggest Feedback - Permalink
What are the near common issues with the latest stable version of Tor Browser?
Whenever we release a new stable version of Tor Browser, we write a blog post that details its new features and known issues. If you started having problems with your Tor Browser after an update, check out blog.torproject.org for a postal service on the about recent stable Tor Browser to see if your outcome is listed. If your issue is not listed there, please check get-go Tor Browser'south issue tracker and create a GitLab issue about what yous're experiencing.
- Edit this page - Propose Feedback - Permalink
I demand Tor Browser in a language that's non English.
Are at that place any paid versions of Tor Browser?
No, Tor Browser is an open source software and it is complimentary. Whatever browser forcing you to pay and is challenge to be Tor Browser is imitation. To make certain you are downloading the correct Tor Browser visit our download page. Afterwards downloading, you can brand sure that y'all accept the official version of Tor Browser by verifying the signature. If y'all are not able to access our website, and then visit censorship department to get information about alternate style of downloading Tor Browser.
Yous can report faux Tor Browsers on frontdesk@torproject.org
- Edit this page - Advise Feedback - Permalink
Which platforms is Tor Browser available for?
Can I download Tor Browser for Chrome OS?
Unfortunately, nosotros don't yet have a version of Tor Browser for Chrome Bone. Yous could run Tor Browser for Android on Chrome OS. Note that by using Tor Mobile on Chrome Os, y'all will view the mobile (not desktop) versions of websites. However, because nosotros have not audited the app in Chrome OS, we don't know if all the privacy features of Tor Browser for Android volition piece of work well.
- Edit this page - Suggest Feedback - Permalink
Is there back up for *BSD?
How tin can I brand Tor run faster? Is Tor Browser slower than other browsers?
Using Tor Browser tin sometimes be slower than other browsers. The Tor network has over a one thousand thousand daily users, and just over 6000 relays to road all of their traffic, and the load on each server tin can sometimes crusade latency. And, by design, your traffic is bouncing through volunteers' servers in various parts of the world, and some bottlenecks and network latency will ever be nowadays. You lot can aid better the speed of the network past running your own relay, or encouraging others to do and so. For the much more in-depth answer, see Roger's blog mail service on the topic and Tor's Open up Enquiry Topics: 2018 edition nigh Network Functioning. That said, Tor is much faster than it used to exist and you may not actually notice any change in speed from other browsers.
- Edit this page - Suggest Feedback - Permalink
What is the divergence between using Tor Browser and 'Incognito fashion' or private tabs?
While the names may imply otherwise, 'Incognito way' and 'private tabs' do not brand yous anonymous on the Internet. They erase all the data on your auto relating to the browsing session afterwards they are closed, but have no measures in place to hide your action or digital fingerprint online. This means that an observer tin can collect your traffic merely equally easily as any regular browser.
Tor Browser offers all the amnesic features of individual tabs while also hiding the source IP, browsing habits and details about a device that can exist used to fingerprint action beyond the web, allowing for a truly private browsing session that'due south fully obfuscated from end-to-terminate.
For more data regarding the limitations of Incognito mode and private tabs, see Mozilla'southward article on Common Myths almost Private Browsing.
- Edit this page - Suggest Feedback - Permalink
Can I set up Tor Browser as my default browser?
In that location are methods for setting Tor Browser as your default browser, but those methods may not work ever or in every operating system. The Tor Browser works hard to isolate itself from the rest of your system, and the steps for making it the default browser are unreliable. This means sometimes a website would load in the Tor Browser, and sometimes it would load in another browser. This blazon of beliefs can be dangerous and intermission anonymity.
- Edit this page - Suggest Feedback - Permalink
Can I utilize Tor with a browser besides Tor Browser?
Nosotros strongly recommend against using Tor in any browser other than Tor Browser. Using Tor in some other browser can leave you vulnerable without the privacy protections of Tor Browser.
- Edit this folio - Suggest Feedback - Permalink
Can I yet employ some other browser, like Chrome or Firefox, when I am using Tor Browser?
You tin can certainly use some other browser while you are also using Tor Browser. However, you should know that the privacy properties of Tor Browser will not be present in the other browser. Be conscientious when switching back and forth between Tor and a less condom browser, considering you may accidentally use the other browser for something you intended to practise using Tor.
- Edit this page - Advise Feedback - Permalink
Is information technology safety to run Tor Browser and some other browser at the aforementioned fourth dimension?
If you run Tor Browser and another browser at the same time, it won't bear on Tor'south performance or privacy properties. However, be aware that your other browser is not keeping your activity individual, and yous may forget and accidentally use that non-private browser to do something that y'all intended to exercise in Tor Browser.
- Edit this folio - Suggest Feedback - Permalink
Does using Tor Browser protect other applications on my computer?
Only Tor Browser's traffic will be routed over the Tor network. Whatsoever other application on your system (including other browsers) will not have their connections routed over the Tor network, and will not be protected. They need to exist configured separately to utilise Tor. If y'all demand to exist sure that all traffic will get through the Tor network, take a look at the Tails live operating arrangement which yous can start on nigh any computer from a USB stick or a DVD.
- Edit this page - Advise Feedback - Permalink
Can I run multiple instances of Tor Browser?
Why does my Tor Browser say something well-nigh Firefox not working?
Why is Tor Browser built from Firefox and non some other browser?
Tor Browser is a modified version of Firefox specifically designed for use with Tor. A lot of piece of work has been put into making the Tor Browser, including the employ of extra patches to enhance privacy and security. While it is technically possible to use Tor with other browsers, you may open yourself up to potential attacks or information leakage, so we strongly discourage it. Learn more about the blueprint of Tor Browser.
- Edit this page - Suggest Feedback - Permalink
How can I export and import bookmarks in Tor Browser?
Bookmarks in the Tor Browser can be exported, imported, backed up, restored as well as imported from some other browser. In order to manage your bookmarks in Tor Browser, go to:
- Hamburger menu >> Library >> Bookmarks >> Show All Bookmarks (below the bill of fare)
- From the toolbar on the Library window, click Import and Backup
If you wish to export bookmarks
- Cull Consign Bookmarks to HTML
- In the Consign Bookmarks File window that opens, choose a location to save the file, which is named bookmarks.html past default. The desktop is usually a good spot, just whatever place that is like shooting fish in a barrel to recall will work.
- Click the Relieve button. The Export Bookmarks File window will close.
- Close the Library window.
Your bookmarks are now successfully exported from Tor Browser. The bookmarks HTML file you saved is now ready to be imported into another spider web browser.
If y'all wish to import bookmarks
- Choose Import Bookmarks from HTML
- Within the Import Bookmarks File window that opens, navigate to the bookmarks HTML file you are importing and select the file.
- Click the Open up button. The Import Bookmarks File window will shut.
- Close the Library window.
The bookmarks in the selected HTML file volition exist added to your Tor Browser within the Bookmarks Card directory.
If you wish to fill-in
- Cull Backup
- A new window opens and you have to choose the location to save the file. The file has a .json extension.
If you wish to restore
- Choose Restore and then select the bookmark file you wish to restore.
- Click okay to the pop upwardly box that appears and hurray, y'all just restored your backup bookmark.
Import data from another browser
Bookmarks tin can exist transferred from Firefox to Tor Browser. At that place are two ways to consign and import bookmarks in Firefox: HTML file or JSON file. After exporting the data from the browser, follow the above step to import the bookmark file into your Tor Browser.
Annotation: Currently, on Tor Browser for Android, there is no good fashion to consign and import bookmarks. Bug #31617
- Edit this page - Suggest Feedback - Permalink
How do I view Tor Browser message log?
When you have Tor Browser open, you tin navigate to the hamburger menu ("≡"), and so click on "Preferences", and finally on "Tor" in the side bar. At the bottom of the page, adjacent to the "View the Tor logs" text, click the push "View Logs...". Y'all should run into an option to copy the log to your clipboard, which you will be able to paste it into a text editor or an email customer.
Alternatively, on GNU/Linux, to view the logs right in the terminal, navigate to the Tor Browser directory and launch the Tor Browser from the command line by running:
./start-tor-browser.desktop --verbose
or to salve the logs to a file (default: tor-browser.log)
./starting time-tor-browser.desktop --log [file]
- Edit this page - Propose Feedback - Permalink
What are grayness bars on resized Tor Browser window?
Tor Browser in its default mode is starting with a content window rounded to a multiple of 200px x 100px to foreclose fingerprinting the screen dimensions. The strategy here is to put all users in a couple of buckets to make it harder to unmarried them out. That works and then far until users start to resize their windows (e.g. by maximizing them or going into fullscreen mode). Tor Browser ships with a fingerprinting defense for those scenarios too, which is called Letterboxing, a technique adult by Mozilla and presented in 2019. It works by adding white margins to a browser window then that the window is equally close every bit possible to the desired size while users are still in a couple of screen size buckets that prevent singling them out with the help of screen dimensions.
In simple words, this technique makes groups of users of certain screen sizes and this makes it harder to single out users on basis of screen size, as many users will have aforementioned screen size.
- Edit this page - Advise Feedback - Permalink
Our website is blocked past a censor. Can Tor Browser help users access our website?
A website I am trying to reach is blocking admission over Tor.
Sometimes websites will block Tor users because they can't tell the difference between the average Tor user and automated traffic. The all-time success we've had in getting sites to unblock Tor users is getting users to contact the site administrators directly. Something like this might practice the trick:
"Hello! I tried to access your site xyz.com while using Tor Browser and discovered that y'all don't allow Tor users to admission your site. I urge you lot to reconsider this decision; Tor is used past people all over the earth to protect their privacy and fight censorship. By blocking Tor users, you lot are likely blocking people in repressive countries who want to use a free net, journalists and researchers who want to protect themselves from discovery, whistleblowers, activists, and ordinary people who desire to opt out of invasive third party tracking. Please take a stiff stance in favor of digital privacy and net freedom, and allow Tor users access to xyz.com. Thank you."
In the case of banks, and other sensitive websites, it is also common to meet geography-based blocking (if a bank knows y'all generally admission their services from one country, and of a sudden you are connecting from an exit relay on the other side of the world, your account may exist locked or suspended).
If you are unable to connect to an onion service, please see I cannot accomplish X.onion!.
- Edit this page - Suggest Feedback - Permalink
A website I am trying to achieve is blocking access over Tor.
Sometimes websites volition block Tor users because they can't tell the difference betwixt the boilerplate Tor user and automated traffic. The best success we've had in getting sites to unblock Tor users is getting users to contact the site administrators directly. Something like this might do the trick:
"Hi! I tried to access your site xyz.com while using Tor Browser and discovered that you lot don't allow Tor users to admission your site. I urge y'all to reconsider this decision; Tor is used past people all over the globe to protect their privacy and fight censorship. By blocking Tor users, you are probable blocking people in repressive countries who want to use a free internet, journalists and researchers who desire to protect themselves from discovery, whistleblowers, activists, and ordinary people who want to opt out of invasive 3rd party tracking. Please take a strong stance in favor of digital privacy and internet freedom, and allow Tor users access to xyz.com. Thank you."
In the instance of banks, and other sensitive websites, it is also common to see geography-based blocking (if a bank knows you lot generally access their services from one country, and suddenly you lot are connecting from an exit relay on the other side of the world, your business relationship may be locked or suspended).
If you are unable to connect to an onion service, please come across I cannot accomplish 10.onion!.
- Edit this page - Advise Feedback - Permalink
A website (banking company, email provider, etc.) locks me out whenever I employ Tor, what can I do?
Tor Browser oftentimes makes your connection appear equally though it is coming from an entirely dissimilar part of the world. Some websites, such as banks or email providers, might interpret this as a sign that your account has been compromised, and lock you out.
The only fashion to resolve this is by following the site'due south recommended procedure for account recovery, or contacting the operators and explaining the situation.
You may exist able to avoid this scenario if your provider offers ii-factor hallmark, which is a much ameliorate security option than IP-based reputations. Contact your provider and ask them if they provide 2FA.
- Edit this page - Suggest Feedback - Permalink
I'm having problem using features on Facebook, Twitter, or some other website when I'm using Tor Browser.
Sometimes JavaScript-heavy websites can have functional issues over Tor Browser. The simplest gear up is to click on the Security icon (the small gray shield at the top-right of the screen), then click "Advanced Security Settings..." Set your security to "Standard".
- Edit this page - Suggest Feedback - Permalink
My antivirus or malware protection is blocking me from accessing Tor Browser.
Most antivirus or malware protection allows the user to "allowlist" sure processes that would otherwise be blocked. Delight open your antivirus or malware protection software and look in the settings for a "allowlist" or something like. Side by side, exclude the following processes:
- For Windows
- firefox.exe
- tor.exe
- obfs4proxy.exe (if you apply bridges)
- snowflake-customer.exe
- For macOS
- TorBrowser
- tor.real
- obfs4proxy (if you use bridges)
- snowflake-client
Finally, restart Tor Browser. This should set the issues you're experiencing. Please annotation that some antivirus clients, like Kaspersky, may also be blocking Tor at the firewall level.
- Edit this folio - Suggest Feedback - Permalink
Tor Browser and antivirus fake positive warnings
Some antivirus software will pop up malware and/or vulnerability warnings when Tor Browser is launched. If you downloaded Tor Browser from our main website or used GetTor, and verified it, these are false positives and y'all have nil to worry about. Some antiviruses consider that files that accept not been seen by a lot of users every bit suspicious. To brand sure that the Tor program you download is the one nosotros take created and has not been modified by some aggressor, you can verify Tor Browser's signature. You may as well want to permit certain processes to forestall antiviruses from blocking access to Tor Browser.
- Edit this page - Suggest Feedback - Permalink
I tin can't connect to Tor Browser, is my network censored?
You might exist on a network that is blocking the Tor network, and so yous should try using bridges. Some bridges are built in to Tor Browser and requires only a few steps to enable it. When you open up Tor Browser for the first time, click "Tor Network Settings". Under the "Bridges" section, select the checkbox "Apply a bridge", and cull the "Select a built-in bridge" option. From the dropdown, select whichever pluggable send you'd like to utilise. One time yous've selected the pluggable send, roll upward and click "Connect" to save your settings.
Or, if you accept Tor Browser running, click on "Preferences" (or "Options" on Windows) in the hamburger bill of fare (≡) and then on "Tor" in the sidebar. In the "Bridges" department, select the checkbox "Utilize a span", and from the option "Select a built-in bridge", choose whichever pluggable transport you lot'd similar to utilise from the dropdown. Your settings volition automatically be saved one time you lot shut the tab.
If you demand other bridges, you lot tin get them at our Bridges website. For more than information virtually bridges, run into the Tor Browser manual.
- Edit this page - Advise Feedback - Permalink
Tor Browser won't connect, only it doesn't seem to be an consequence with censorship.
1 of the most common issues that causes connectedness errors in Tor Browser is an incorrect system clock. Please make sure your system clock and timezone are prepare accurately. If this doesn't set the problem, see the Troubleshooting folio on the Tor Browser manual.
- Edit this page - Advise Feedback - Permalink
Gmail warns me that my account may have been compromised
Sometimes, after yous've used Gmail over Tor, Google presents a pop-up notification that your business relationship may have been compromised. The notification window lists a series of IP addresses and locations throughout the world recently used to access your account.
In full general, this is a false alarm: Google saw a bunch of logins from different places, as a result of running the service via Tor, and decided it was a good idea to confirm the business relationship was being accessed by its rightful owner.
Even though this may be a byproduct of using the service via Tor, that doesn't mean you tin entirely ignore the warning. It is probably a false positive, but it might not be since information technology is possible for someone to hijack your Google cookie.
Cookie hijacking is possible by either physical admission to your computer or past watching your network traffic. In theory, only physical access should compromise your system because Gmail and similar services should but send the cookie over an SSL link. In exercise, alas, it's way more complex than that.
And if somebody did steal your Google cookie, they might end up logging in from unusual places (though of course they also might non). So the summary is that since you're using Tor Browser, this security mensurate that Google uses isn't so useful for y'all, because it's full of false positives. You'll have to utilise other approaches, like seeing if anything looks weird on the account, or looking at the timestamps for contempo logins and wondering if you lot really logged in at those times.
More recently, Gmail users tin plough on 2-Step Verification on their accounts to add an extra layer of security.
- Edit this page - Suggest Feedback - Permalink
Google makes me solve a Captcha or tells me I have spyware installed
This is a known and intermittent problem; it does not hateful that Google considers Tor to be spyware.
When you use Tor, you are sending queries through exit relays that are too shared by thousands of other users. Tor users typically see this message when many Tor users are querying Google in a short menstruum of time. Google interprets the loftier volume of traffic from a single IP address (the exit relay yous happened to pick) as somebody trying to "crawl" their website, and then it slows down traffic from that IP accost for a short time.
You can try 'alter the circuit for this site' to access the website from a different IP accost.
An alternate explanation is that Google tries to detect certain kinds of spyware or viruses that ship distinctive queries to Google Search. It notes the IP addresses from which those queries are received (non realizing that they are Tor exit relays), and tries to warn any connections coming from those IP addresses that recent queries bespeak an infection.
To our noesis, Google is not doing anything intentionally specifically to deter or block Tor use. The error message about an infected machine should clear up once more later on a short fourth dimension.
- Edit this page - Suggest Feedback - Permalink
Tin can you get rid of all the Captchas?
Unfortunately, some websites evangelize Captchas to Tor users, and we are not able to remove Captchas from websites. The best thing to practise in these cases is to contact the website owners, and inform them that their Captchas are preventing users such equally yourself from using their services.
- Edit this page - Suggest Feedback - Permalink
Why does Google evidence up in foreign languages?
Google uses "geolocation" to determine where in the world yous are, and so it tin can requite you lot a personalized feel. This includes using the language it thinks y'all prefer, and it also includes giving yous unlike results on your queries.
If y'all actually want to encounter Google in English you can click the link that provides that. But we consider this a feature with Tor, not a problems --- the Net is not flat, and information technology in fact does look unlike depending on where you are. This feature reminds people of this fact.
Notation that Google search URLs take name/value pairs every bit arguments and one of those names is "hl". If yous set "hl" to "en" then Google will return search results in English regardless of what Google server yous accept been sent to. The changed link might look like this:
https://encrypted.google.com/search?q=online%20anonymity&hl=en
Another method is to simply use your country code for accessing Google. This can exist google.exist, google.de, google.u.s.a. and so on.
- Edit this folio - Suggest Feedback - Permalink
Will my network admin be able to tell I'one thousand using Tor Browser?
When using Tor Browser, no one tin can see the websites that you lot visit. However, your service provider or network admins may be able to see that you're connecting to the Tor network, though they won't know what y'all're doing when y'all become there.
- Edit this folio - Suggest Feedback - Permalink
When I utilise Tor Browser, will anyone be able to tell which websites I visit?
Tor Browser prevents people from knowing the websites you visit. Some entities, such every bit your Internet Service Provider (ISP), may be able to see that yous're using Tor, but they won't know where you're going when you practice.
- Edit this page - Advise Feedback - Permalink
What search engine comes with Tor Browser and how does it protect my privacy?
Why did my search engine switch to DuckDuckGo?
With the release of Tor Browser 6.0.6, nosotros switched to DuckDuckGo as the primary search engine. For a while at present, Disconnect, which was formerly used in Tor Browser, has had no access to Google search results. Since Disconnect is more of a meta search engine, which allows users to choose between unlike search providers, it fell back to delivering Bing search results, which were basically unacceptable quality-wise. DuckDuckGo does not log, collect or share the user's personal data or their search history, and therefore is all-time positioned to protect your privacy. Most other search engines store your searches along with other data such as the timestamp, your IP accost, and your business relationship information if you are logged in.
- Edit this folio - Advise Feedback - Permalink
I'thou having a problem with DuckDuckGo.
Is there a way to change the IP address that Tor Browser assigns me for a particular site?
Tor Browser has ii means to change your relay circuit — "New Identity" and "New Tor Circuit for this Site". Both options are located in the hamburger menu ("≡"). Yous can likewise access the New Circuit pick inside the site information carte du jour in the URL bar, and the New Identity option by clicking the small sparky broom icon at the top-correct of the screen.
New Identity
This option is useful if you lot desire to prevent your subsequent browser activity from existence linkable to what you were doing before.
Selecting it volition close all your tabs and windows, clear all individual information such as cookies and browsing history, and use new Tor circuits for all connections.
Tor Browser volition warn y'all that all activity and downloads will be stopped, so accept this into account before clicking "New Identity".
New Tor Circuit for this Site
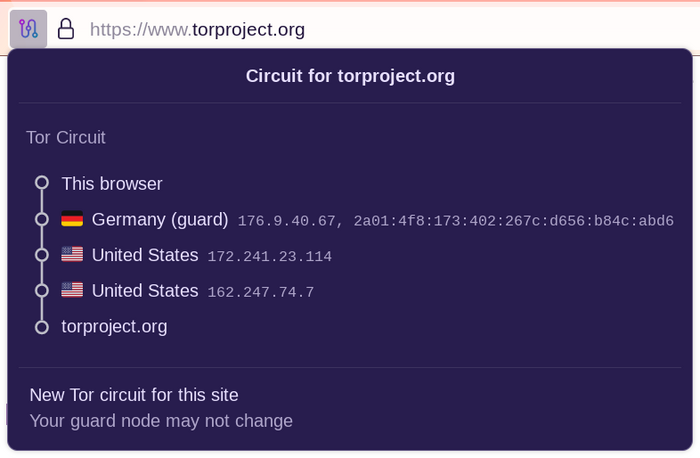
This option is useful if the exit relay you are using is unable to connect to the website you require, or is not loading it properly. Selecting it will crusade the currently-active tab or window to exist reloaded over a new Tor circuit.
Other open tabs and windows from the same website volition use the new circuit besides one time they are reloaded.
This option does not articulate any individual information or unlink your activity, nor does it affect your electric current connections to other websites.
- Edit this page - Suggest Feedback - Permalink
Does running Tor Browser make me a relay?
Why is the first IP address in my relay circuit e'er the same?
That is normal Tor beliefs. The first relay in your circuit is called an "entry guard" or "baby-sit". Information technology is a fast and stable relay that remains the first one in your circuit for 2-3 months in order to protect against a known anonymity-breaking set on. The remainder of your excursion changes with every new website you visit, and all together these relays provide the full privacy protections of Tor. For more information on how guard relays piece of work, encounter this web log post and newspaper on entry guards.
- Edit this page - Suggest Feedback - Permalink
Does Tor Browser utilise a different circuit for each website?
Can I pick which country I'1000 exiting from?
Modifying the style that Tor creates its circuits is strongly discouraged. Y'all get the all-time security that Tor can provide when you lot leave the route option to Tor; overriding the entry/exit nodes can compromise your anonymity. If the result you lot desire is but to be able to admission resources that are only available in one country, you may want to consider using a VPN instead of using Tor. Please notation that VPNs practice not accept the same privacy properties every bit Tor, only they will aid solve some geolocation restriction issues.
- Edit this page - Advise Feedback - Permalink
I'm supposed to "edit my torrc". What does that mean?
Warning: Do NOT follow random advice instructing you to edit your torrc! Doing then tin permit an assaulter to compromise your security and anonymity through malicious configuration of your torrc.
Tor uses a text file called torrc that contains configuration instructions for how Tor should conduct. The default configuration should work fine for most Tor users (hence the warning in a higher place.)
To find your Tor Browser torrc, follow the instructions for your operating organisation beneath.
On Windows or Linux:
- The
torrcis in the Tor Browser Data directory atBrowser/TorBrowser/Information/Torinside your Tor Browser directory.
On macOS:
- The
torrcis in the Tor Browser Data directory at~/Library/Application Support/TorBrowser-Data/Tor. - Note the Library binder is hidden on newer versions of macOS. To navigate to this binder in Finder, select "Become to Folder..." in the "Get" menu.
- Then type
~/Library/Application Support/in the window and click Go.
Close Tor Browser before you edit your torrc, otherwise Tor Browser may erase your modifications. Some options volition have no consequence as Tor Browser overrides them with command line options when information technology starts Tor.
Accept a look at the sample torrc file for hints on common configurations. For other configuration options you tin use, encounter the Tor transmission page. Call back, all lines beginning with # in torrc are treated every bit comments and take no effect on Tor'southward configuration.
- Edit this page - Suggest Feedback - Permalink
Should I install a new addition or extension in Tor Browser, like AdBlock Plus or uBlock Origin?
Information technology'due south strongly discouraged to install new add-ons in Tor Browser, because they can compromise your privacy and security.
Installing new add-ons may affect Tor Browser in unforeseen ways and potentially make your Tor Browser fingerprint unique. If your copy of Tor Browser has a unique fingerprint, your browsing activities tin be deanonymized and tracked even though you are using Tor Browser.
Basically, each browser's settings and features create what is chosen a "browser fingerprint". Most browsers inadvertently create a unique fingerprint for each user which can be tracked beyond the internet. Tor Browser is specifically engineered to have a nearly identical (nosotros're non perfect!) fingerprint across its users. This ways each Tor Browser user looks similar every other Tor Browser user, making it hard to track any individual user.
There'due south as well a good chance a new add-on will increment the attack surface of Tor Browser. This may allow sensitive data to be leaked or let an attacker to infect Tor Browser. The addition itself could fifty-fifty exist maliciously designed to spy on you.
Tor Browser already comes installed with two add-ons — HTTPS Everywhere and NoScript — and calculation anything else could deanonymize yous.
Want to learn more about browser fingerprinting? Here's an article on The Tor Web log all about it.
- Edit this page - Propose Feedback - Permalink
Can I use Flash in Tor Browser?
Flash is disabled in Tor Browser, and we recommend you to not enable it. We don't recollect Flash is condom to utilize in any browser — it's a very insecure piece of software that tin easily compromise your privacy or serve you malware. Fortunately, most websites, devices, and other browsers are moving away from the apply of Flash.
- Edit this folio - Suggest Feedback - Permalink
My net connection requires an HTTP or SOCKS Proxy
If you're using Tor Browser, you can set up your proxy's address, port, and authentication information in the Network Settings.
If you're using Tor another mode, you tin set the proxy information in your torrc file. Cheque out the HTTPSProxy config option in the manual folio. If your proxy requires authentication, see the HTTPSProxyAuthenticator option. Example with hallmark:
HTTPSProxy 10.0.0.1:8080 HTTPSProxyAuthenticator myusername:mypass Nosotros only support Basic auth currently, but if you need NTLM authentication, y'all may find this post in the athenaeum useful.
For using a SOCKS proxy, see the Socks4Proxy, Socks5Proxy, and related torrc options in the manual page. Using a SOCKS 5 proxy with authentication might expect like this:
Socks5Proxy 10.0.0.one:1080 Socks5ProxyUsername myuser Socks5ProxyPassword mypass If your proxies only allow you to connect to certain ports, look at the entry on Firewalled clients for how to restrict what ports your Tor will endeavour to admission.
- Edit this page - Propose Feedback - Permalink
My firewall only allows a few outgoing ports
If your firewall works by blocking ports, then you can tell Tor to only use the ports when you start your Tor Browser. Or you lot tin add the ports that your firewall permits past adding "FascistFirewall 1" to your torrc configuration file. By default, when you set this Tor assumes that your firewall allows only port 80 and port 443 (HTTP and HTTPS respectively). Y'all tin can select a different gear up of ports with the FirewallPorts torrc option. If yous want to be more fine-grained with your controls, you can also use the ReachableAddresses config options, e.g.:
ReachableDirAddresses *:80 ReachableORAddresses *:443 - Edit this folio - Suggest Feedback - Permalink
I'm having a problem with HTTPS Everywhere.
Why does Tor Browser ship with JavaScript enabled?
We configure NoScript to permit JavaScript by default in Tor Browser because many websites volition not work with JavaScript disabled. Most users would surrender on Tor entirely if nosotros disabled JavaScript by default considering it would crusade and then many bug for them. Ultimately, we desire to make Tor Browser as secure as possible while also making information technology usable for the majority of people, and then for now, that ways leaving JavaScript enabled by default.
For users who want to have JavaScript disabled on all HTTP sites by default, we recommend changing your Tor Browser's "Security Level" option. This can be done past navigating the Security icon (the pocket-size greyness shield at the superlative-right of the screen), then clicking "Advanced Security Settings...". The "Standard" level allows JavaScript, merely the "Safer" and "Safest" levels both cake JavaScript on HTTP sites.
- Edit this folio - Suggest Feedback - Permalink
I want to run my Tor client on a different estimator than my applications
By default, your Tor client only listens for applications that connect from localhost. Connections from other computers are refused. If yous want to torify applications on unlike computers than the Tor client, you should edit your torrc to define SocksListenAddress 0.0.0.0 then restart (or hup) Tor. If you want to get more than avant-garde, you can configure your Tor client on a firewall to bind to your internal IP but not your external IP.
- Edit this page - Suggest Feedback - Permalink
Can I install Tor on a central server, and take my clients connect to it?
Yes. Tor tin can be configured as a client or a relay on another machine, and allow other machines to be able to connect to it for anonymity. This is well-nigh useful in an environs where many computers desire a gateway of anonymity to the residue of the earth. However, be forewarned that with this configuration, anyone within your individual network (existing between you and the Tor customer/relay) can see what traffic you are sending in clear text. The anonymity doesn't start until y'all go to the Tor relay. Because of this, if you are the controller of your domain and you know everything's locked down, you will be OK, but this configuration may not be suitable for large individual networks where security is key all around.
Configuration is unproblematic, editing your torrc file's SocksListenAddress according to the post-obit examples:
SocksListenAddress 127.0.0.i SocksListenAddress 192.168.x.x:9100 SocksListenAddress 0.0.0.0:9100 You can land multiple listen addresses, in the case that you are function of several networks or subnets.
SocksListenAddress 192.168.x.x:9100 #eth0 SocksListenAddress ten.x.10.x:9100 #eth1 After this, your clients on their corresponding networks/subnets would specify a socks proxy with the address and port you specified SocksListenAddress to be. Please notation that the SocksPort configuration option gives the port ONLY for localhost (127.0.0.1). When setting up your SocksListenAddress(es), y'all need to give the port with the address, as shown higher up. If you are interested in forcing all outgoing data through the central Tor client/relay, instead of the server only being an optional proxy, you lot may find the program iptables (for *nix) useful.
- Edit this folio - Advise Feedback - Permalink
I'm having a problem with NoScript.
pattersonwaris1961.blogspot.com
Source: https://support.torproject.org/
0 Response to "Having Trouble Uploading Photo to Twitter Using Tor Browser"
Post a Comment